How end to end encryption works?
This process of encryption by creating a public-private key pair is known as ‘asymmetric cryptography’. The separate cryptographic keys that are used to encrypt and decrypt data are stored on the endpoints. Public keys are widely distributed and are used to lock or encrypt a message. Private keys are only known by the owner and are used to unlock or decrypt the message. In end-to-end encryption, the system creates public and private cryptographic keys for each person who joins.
How end to end encryption differs from other encryption?
Unlike standard encryption methods, end-to-end encryption has a higher level of data privacy which is provided by the following features:
- Compliance- Due to compliance regulations and laws, encryption-level data security is usually required for a business. End-to-end encryption will allow an organization to protect its data by making it completely unreadable to external parties.
- Security in transit- end-to-end encryption uses public key cryptography with the private key accessible at the endpoint device. Data can only be decrypted using these keys meaning it is completely secure in transit and can only be accessed at the endpoint device.
- Tamper-proof- the decryption key is not transmitted with end-to-end encryption as the recipient will already have it. If the data that has been encrypted with the public key gets tampered with in transit, the recipient can not decrypt this and so the tampered content will not be viewable.
Why end to end encryption matters during a migration to Microsoft 365?
Migrating to cloud infrastructure for the first time can be challenging. Given the volume of logistics and planning involved in the migration, the security of data during the process needs to be heavily considered.
At CloudM, security requirements and legislations are at the front of out mind during every migration. Having end to end encryption in our self hosted environment will meet any security regulation and more.
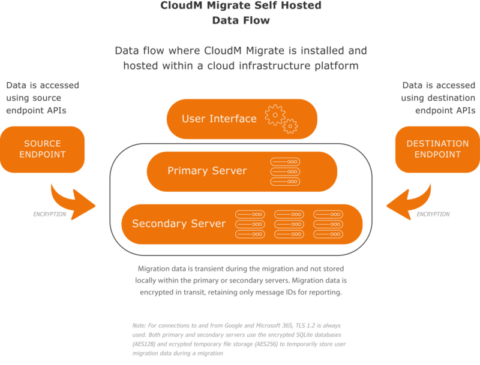
CloudM Migrate already has end-to-end encryption between migration endpoints. The option to Self Host CloudM Migrate will completely isolate your migration data from your source environment to the destination cloud tenant.
Data Storage with CloudM
Both primary and secondary servers use the following components to temporarily store migration data during a migration.
- Encrypted SQLite databases (AES256)
- Encrypted temporary file storage (AES256)
Other project-related data is provided by:
- SQLite databases
- SQL Server – Server 2019 Express is installed by default, or a customer can specify their own SQL Server.
- Redis – Installed as part of the CloudM Migrate installation process.
All of these store non-sensitive data such as item IDs in order to provide reporting on migrations.
Where CloudM Migrate requires a username or password to interact with a system, and stores sensitive data like this, that data is stored encrypted within SQL Server (AES256). SQL Server 2019 Express is installed by default but you can specify your own SQL instance.
Migrations are a specialized area, bringing with them their own challenges and solutions, and the right advice from experts like us can make things go a lot smoother. It’s important to understand your limitations, as mishandling a migration can have disastrous consequences.
We know how important security is during migrations. Move to the cloud with confidence with guaranteed data integrity with zero downtime for users with our secure cloud migration tool..